frontpageDr.W posted Nov 16, 2025 04:11 AM
Item 1 of 4
Item 1 of 4
frontpageDr.W posted Nov 16, 2025 04:11 AM
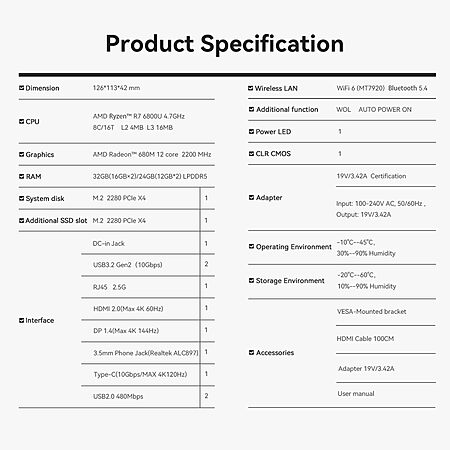
Beelink SER5 MAX Mini PC: Ryzen 7 6800U, 24GB RAM, 500GB SSD, Win 11 Pro
+ Free Shipping$299
$419
28% offAmazon
Get Deal at AmazonGood Deal
Bad Deal
Save
Share



Leave a Comment
Top Comments
https://arstechnica.com/informati...ein
There is a very big discussion to be had here about risks, costs, feasibility etc, but at the end of the day, the chances of hardware containing low-level and hardware-level malware being sold on websites like Amazon are greater every day. The technology has been proliferating since the early 10s, we've seen backdoors in name brand consumer-grade networking equipment (TP-Link and Netgear), we've seen bundled OS malware on "name brand" mini (Acemagician) PCs. There is practically zero regulation and protection for consumers today. There are enterprise protections for these attack vectors but they are mostly unavailable to end users.
Pragmatically speaking, if you must to buy these Chinese brands of mini PCs and you want to minimize your risk, the safest approach is to install a Linux distro and assume any data you enter will be compromised. At the very least, installing a clean copy of Windows has a good chance of wiping out software-level malware and generally speaking that's going to be the cheapest and thus most common attack vector - though it may not work if you have firmware that reloads the malware.
It's kind of funny, even companies like HP have been using their own in-house firmware-level malware that auto loads their invasive telemetry into Windows since at least the mid 10s. It isn't super sophisticated but you have to run an agent or scripts to constantly keep it from re-enabling itself.
Just be wary of people telling you to blindly trust these companies, most of them are just parroting things they want to hear.
78 Comments
Sign up for a Slickdeals account to remove this ad.
Our community has rated this post as helpful. If you agree, why not thank ROB.E.REIN
https://www.reddit.com/r/BeelinkO...n_7_
Sign up for a Slickdeals account to remove this ad.
https://www.reddit.com/r/BeelinkO...dp_i
Our community has rated this post as helpful. If you agree, why not thank TACO_Trader
https://www.reddit.com/r/BeelinkO...dp_i
Missed the last GMKtec deal but hoping for one on BF.
Sign up for a Slickdeals account to remove this ad.
Our community has rated this post as helpful. If you agree, why not thank garth25
I've put about 50 of these in client locations and 3 years in they are rock solid.
Leave a Comment